That’s not how code of this magnitude works off the cuff GetPhysicallyInstalledSystemMemory() and GetPhysicalDiskSize()) aren’t defined and might exist in a file they couldn’t access. It’s also in C++ so you’d have to compile it first no one’s going through all that for a visual screenshot of a watermark at this stage
If you want a serious answer, you could theoretically disable all security checks on Win11 so you could hex-edit patch it to run, but it would be (1) a lot of effort and (2) probably show that it’s nowhere near finished, because it still misses UI integration for example
Screenshot?
Read the article? :D Doesn’t look like it’s live they just caught it in code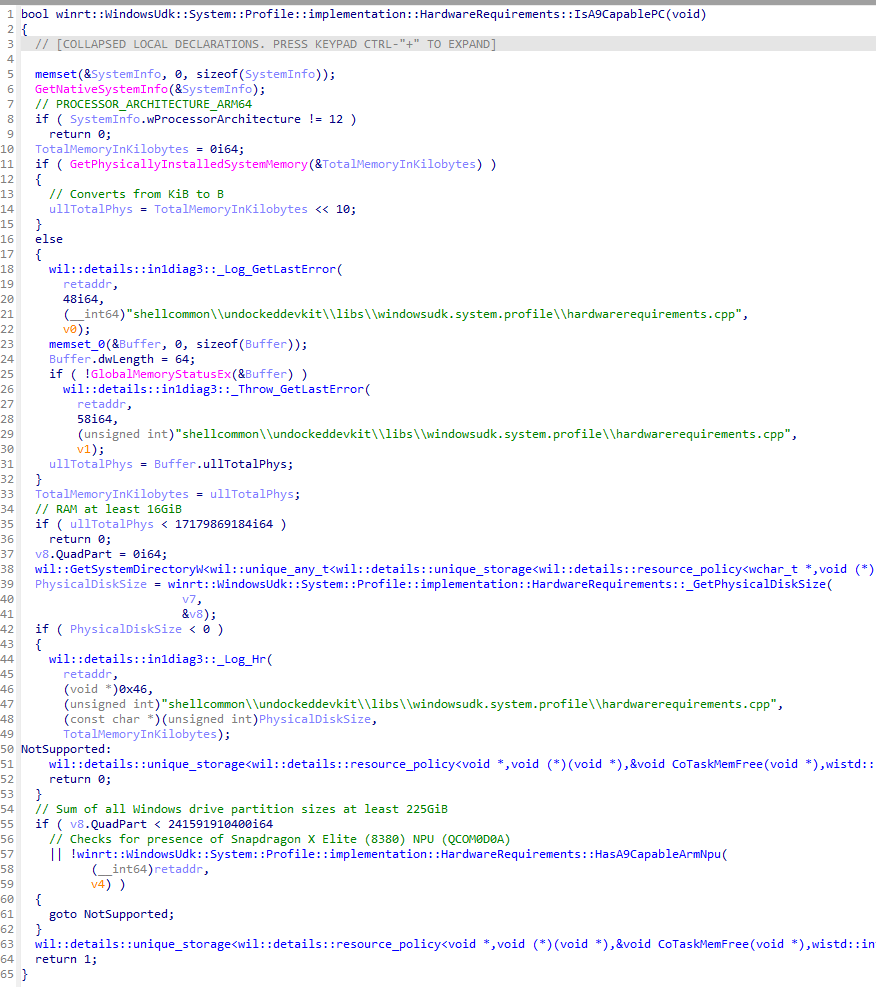
Am I reading correctly that ARM is required?
This might be only for a WinRT build (Windows mm ARM)
How did they get the code?
Yeah, so if they have the code, they could run it…
That’s not how code of this magnitude works off the cuff GetPhysicallyInstalledSystemMemory() and GetPhysicalDiskSize()) aren’t defined and might exist in a file they couldn’t access. It’s also in C++ so you’d have to compile it first no one’s going through all that for a visual screenshot of a watermark at this stage
Wow that’s some crappy C/C++ code, there’s even a goto 😁
But whats the 0i64?
They kinda don’t have the sources there. That’s a decompilation by IDA in that image.
But nevertheless they could run it if they set up an arm64 machine, technically.
If you want a serious answer, you could theoretically disable all security checks on Win11 so you could hex-edit patch it to run, but it would be (1) a lot of effort and (2) probably show that it’s nowhere near finished, because it still misses UI integration for example