Hardened Grub in Libreboot https://libreboot.org/docs/linux/grub_hardening.html
See Mate Kukri at upcoming Open Source Firmware Conference about TPM compromise.
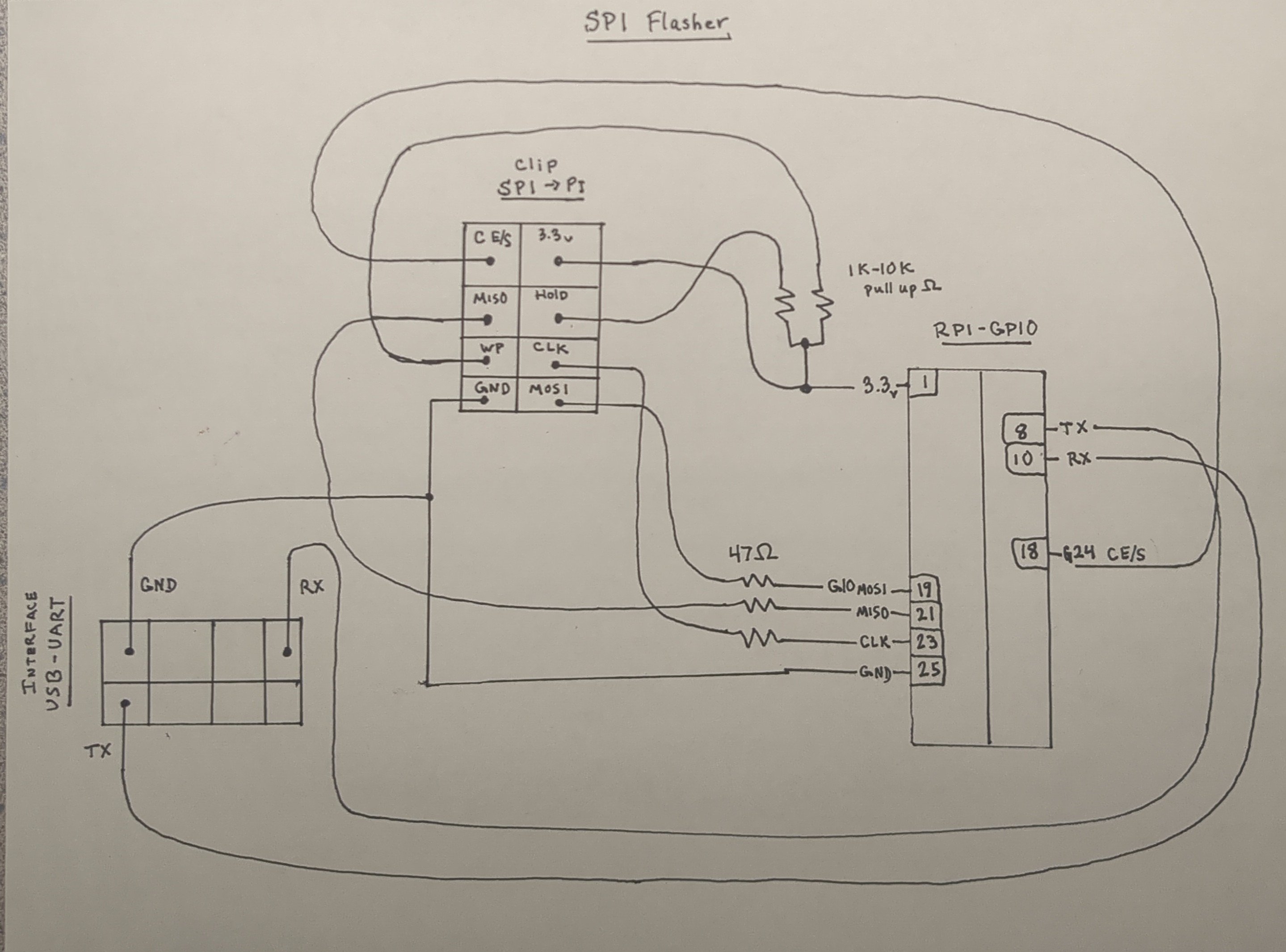
https://libreboot.org/docs/install/spi.html Ready to get out your pi and external programmer? https://en.m.wikipedia.org/wiki/CryptoParty
minicom UART for Pi

SPI connector SOIC8

RPi connects automatically (wpa supplicant) to SSID if you use their imager (not dd) but you need access to the router API to get the pi’s IP (or nmap -sP <network>) and then a script automatically configures the ssh private-public key on first initialization which is default rsa but you can text box in a ssh-keygen ed25591 (521 bit 100+ rounds).
Beagle Bone or some other SBC may be preferable if you want to avoid wireless connections for sensitive firmware operations. Make sure your router is locked down tight because some asshole is supposed to hostile takeover your pi but there is no way for him to do so without an NSA because the ssh crypto curves are strong (no civilian breaks rsa 4096 let alone the newer quantum resistant ed25519).
No way to connect to rpi without peripherals because defaults need to be changed via terminal first for UART serial and WiFi ssh.Editing bootfs and rootfs (unless you want to make time-consuming scripts) won’t do it. This is probably by design since rpis ship with default Google DNS for telemetry and data mining.Suggest changing resolv.conf* so Google doesn’t 8 all your pi before you get some.*After ssh configuration, rpi uses DNS of router.
Plug rpi into power and it will connect automatically with the wpa-supplicant script made by the imager (/NetworkManager/systems connections/preconfigured -connection) and then run the following commands from your laptop connected to the same router.
ip addrinetis ip of <router> (you can even use a cell hotspot) if you want to usenmapsudo bettercap(add wifi module to PCI if you are using Qubes)net.probe on
endpoint.newis ip of pi detected as <MAC>
Login successful!
Most IoT doesn’t need full disk encryption because it is protected physically and what is most important is the private-public key security of ssh for remote login. Rasbian has SELinux enabled and is as secure when connected to networking as most servers with not much additional hardening required (especially if you are flashing firmware and not running an infinite uptime you have to protect from attacks).
 https://en.m.wikipedia.org/wiki/Identicon
https://en.m.wikipedia.org/wiki/Identiconthis cryptography is immune to timing attacks https://en.m.wikipedia.org/wiki/Curve25519
With Raspbian OS on this sbc, you can’t just use
ddbecause of how the OS defaults are set which prevent any interfacing with the pi except via ssh wirelessly (maybe eth0 other models). The openssh scripts are made by Canonical but generated locally (usr/lib/openssh FIRSTUSER) which also means you can’t just configure ssh/sshd.conf. But you can copy a self-generated ssh public key to the imager settings (their default is rsa but your own ed25519 will also work).I recommended configuring your router resolve DNS to cloudflare (with malware filter) or something besides Google8 and also editing the sources list and raspi list to add the S to http.
Then, after you have sshed in, you can update, git clone lbmk, and change the
raspi-configto enable UART. After that, you can proceed hardwired withminicomandrfkillall wireless for extra security.libreboot lbmk acquired successfully!
[note: WP and Hold resistors not required for In-System Programming]