- cross-posted to:
- [email protected]
- technology
- [email protected]
- cross-posted to:
- [email protected]
- technology
- [email protected]
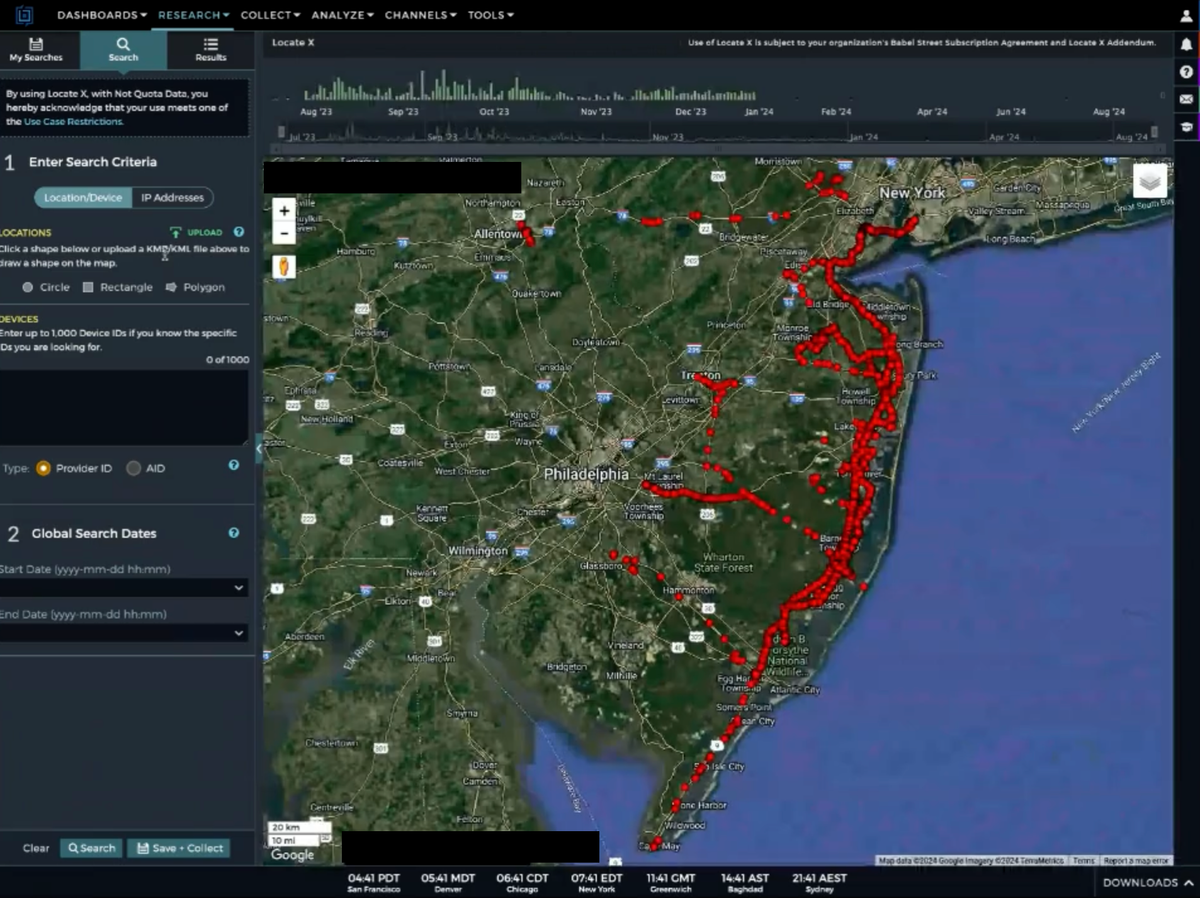
Privacy advocates got access to Locate X, a phone tracking tool which multiple U.S. agencies have bought access to, and showed me and other journalists exactly what it was capable of. Tracking a phone from one state to another to an abortion clinic. Multiple places of worship. A school. Following a likely juror to a residence. And all of this tracking is possible without a warrant, and instead just a few clicks of a mouse.


You have the option to spoof/fake/mock it manually with an app. This one, it seems, even has some available add-ons for mocking UnifiedNlp data and more…)
Mock my GPS (mock the GPS and Network location providers) https://f-droid.org/packages/com.github.warren_bank.mock_location/
Mock my GPS UnifiedNlp Backend (mock the GPS and Network location providers) https://f-droid.org/packages/com.github.warren_bank.mock_location.service.microg_nlp_backend/
Mock Silently (mock the GPS and Network location providers) https://f-droid.org/packages/com.github.warren_bank.mock_location.silently/
Possibly you’ll have to enable dev options and set the location spoofing app in there. At least, I remember seeing the option in there, but that was years ago.
This changes location reported to applications by the OS. It doesn’t change that your signal is coming from a direction and distance as known by the tower tracking the phone. MIMO and other beamforming techniques use this data to boost signal, but it is also collected for monitoring.