- cross-posted to:
- [email protected]
- cross-posted to:
- [email protected]
Apple’s decision to disable the feature for U.K. users could well be the only reasonable response at this point
Hard disagree. The most reasonable response would be to refuse to comply, organize, and fight it in court. But that would cost them money. And they don’t care about their users that much.
Troubling precedent, but I expect no one used this anyways. Anybody who needs this would be smart enough to know not to trust so proprietary a device and service.
Given how
readily Apple has rolled over for law enforcement in the pastloudly Apple has opposed working with law enforcement in the past, only for devices to be magically unlocked anyways, this is (probably) just security theater.Yeah, it’s 3rd party vendors like greykey and cellibrite that allow LEO to get around apples security.
To its credit, apple does a fairly decent job of staying ahead of the unlocking tech, but some older hardware and os are easily cracked.
https://cybersecuritynews.com/phones-cellebrite-tool-can-unlock/
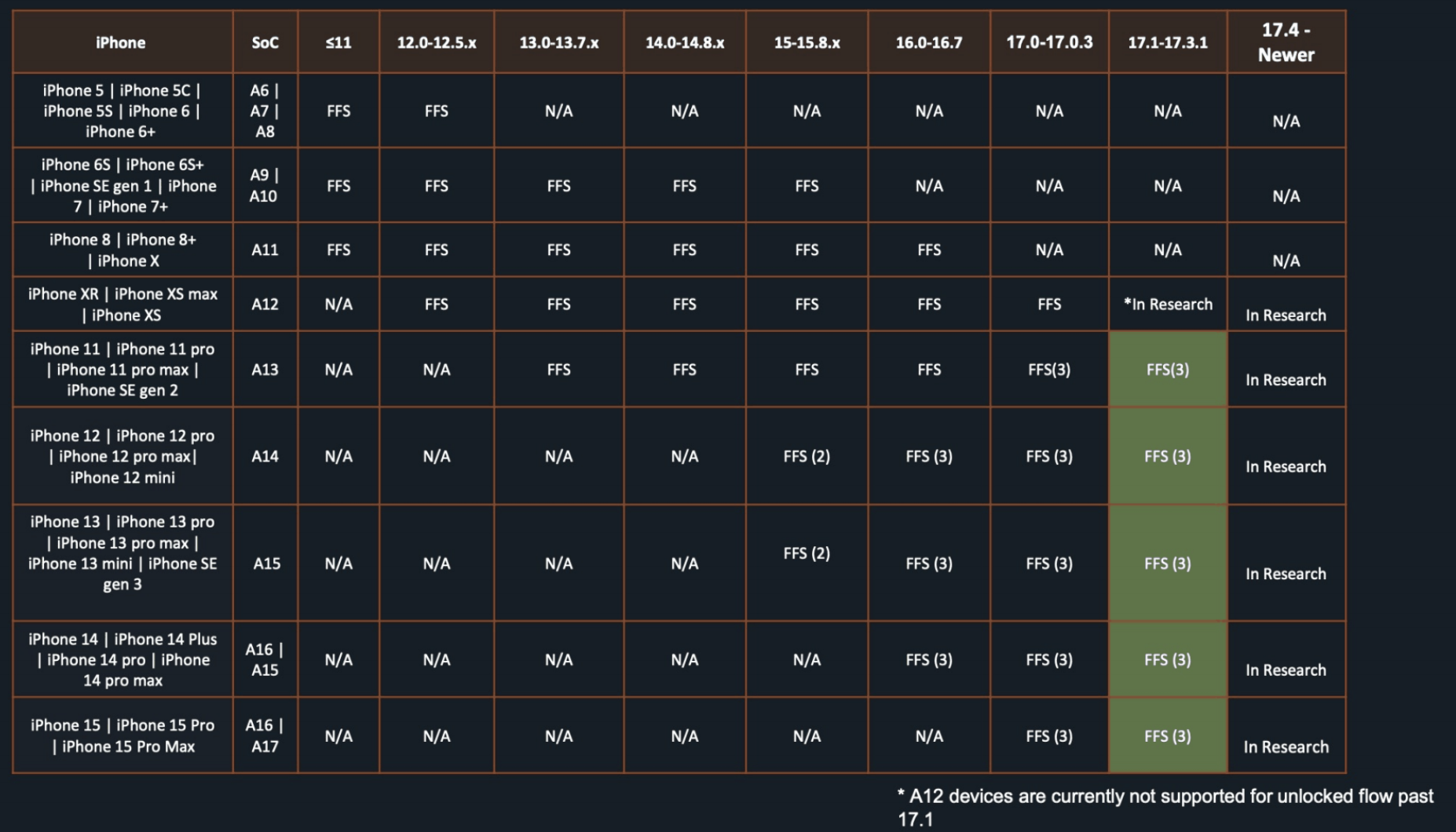

Is this Hardware or software dependent when it comes to Android? Do you know? Curious about whether moving to graphene would even matter.
Edit: Found the following discussion. https://discuss.grapheneos.org/d/14344-cellebrite-premium-july-2024-documentation
It is both. But graphene is the way.
I was reading some of the Graphene forum discussion the other day. Basicaly, grapheme is the only os on any hardware that concerns LEO and courts.
Reading about the one country where when graphene is found on a phone they automatically declare it “uncontrolled” and a “criminal tool”.
Do you have citations for “Apple has rolled over for law enforcement in the past”? I’m wondering if this is country-specific.
Fortunately you can still back up your devices locally, and store your photos locally, and these backups can be encrypted.
I don’t know about other countries, but Apple itself reports that it provided access to customer accounts at the US government’s request 90% of the time
With a warrant. Fortunately end to end encryption is still available in the US (for now).
Sure, but if that’s your only concern, then you aren’t really concerned that the toggle is removed in the UK, either
The report is that Apple is removing the user’s ability to disable Apple’s back door, and you asked for evidence that they roll over for law enforcement
If you want governments to have access to a backdoor to what Apple touts as “Privacy,” your initial question doesn’t make much sense
Your definition of “rolling over” is different than mine.
- They’re requiring a warrant for the information. They don’t just hand over stuff at any request.
- They review the warrant before handing over the data. They don’t provide data in 100% of cases.
- They offer users end to end encryption, which would certainly make it difficult for the data recipient to decrypt if the data is handed over.
- They don’t offer the government a “backdoor” to make it easy to decrypt user data.
- They offer users the option to encrypt and store the data locally rather than uploading it to Apple.
What would you have them do differently when the warrants issued are valid in the legal sense/approved by a judge?
- They don’t offer the government a “backdoor” to make it easy to decrypt user data.
Is what’s being discussed. Since Apple has a backdoor in the default configuration of their phone, they’re able to comply with 90% of all data requests.
The UK is demanding they remove the option to disable the backdoor in their encryption
You can kind-of sort-of use local only, but Apple makes that very inconvenient and almost 0 users do
Your definition of “rolling over” is different than mine. … What would you have them do differently when the warrants issued are valid in the legal sense/approved by a judge?
Again, your comments are agreeing with their decision to not allow full end to end encryption.
I would have them not able to decrypt my data at all
My recollection was erroneous, as I can’t (easily) find evidence of them rolling over. But the devices in question still got unlocked, so in the end it didn’t matter whether Apple (openly or surreptitiously) cooperated.